This time there would be no witnesses. This time there will be just the dead earth, a rumble of thunder and Bob sending Alice his public key in perfect silence because Eve is simply not interested intercepting it… are you all ears? Good 🙂 While trying to take a closer look at the way transactions in Bitcoin work, you’ve probably noticed how content writers always bring up the names of Bob and Alice. Yet, who is Bob? Who is Alice? Are they even people? And why are private and public keys so important for the nature of their long-term relationship?
One more time. You’re going to spill that much ink over Bob and Alice – why, exactly?
take a look at this excerpt from Satoshi’s white paper on Bitcoin
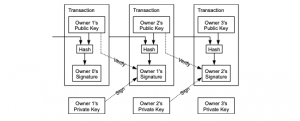
Can you see that teeny-tiny word “transaction” on top of every rectangle?
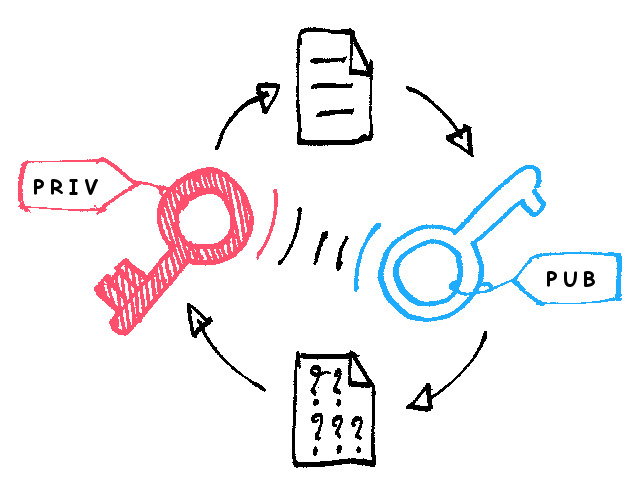
Public blockchains rest on very certain encryption technology, and once you transact money, you unleash high-level maths magic. Basically, you unleash Bob and Alice, a sweet couple of robots that always exchange information, encrypting and decrypting each other’s messages with a private and a public key.
When you send some bitcoins to someone, you, basically, attach the new owner’s public key to this amount of coins. To do that, you sign your transaction with your private key, not a public one.
Still sounds like yada yada yada? This is the reason why we need to spill the ink over Bob and Alice.
“Coz for twenty-four years
I’ve been living next door to Alice”

Actually, we’ve been living next door to this couple for many more years, 40, to be precise.
-Bob and Alice, where do you come from?
-From the chilling world of cryptography!
As early as mid-70s, Ron Rivest, Adi Shamir, and Leonard Adleman invented Bob and Alice as an illustration for highly abstract concepts.

Back in time, the scientists were working on “a method for obtaining digital signatures and public key cryptosystems”. They wanted to demonstrate how two humans can interact with each other in the new paradigm. See, back then, Bob and Alice were still humans. The times They are A Changin’. Later, Eve (an eavesdropper) joined the couple as the person who could passively intercept their encrypted message and decode it without them knowing it.
Cut to the chase and turn Bob and Alice into robots already!
We hear you. But let’s be reasonable! In reality, all the developments in cryptography had taken more than 30 years before Bob and Alice turned into what they are today. Please give them one more chance and deal with two paradigms first – symmetric encryption and asymmetric encryption. Because you need to get to the bottom of where the concept of public key comes from.
“Symmetric encryption” sounds really, really nerdy
It’s a little bit nerdy, right. But once you get it, it will turn out to be fun and easy! Read on, to see how Soviet spies used symmetric encryption during the Cold War!
Symmetric-key algorithms are algorithms for cryptography that use the same cryptographic keys for both, encryption of plaintext and decryption of ciphertext. Speaking plain English, while using this scheme, the sender encrypts the message with a specific key, and a receiver decrypts it with the identical key.
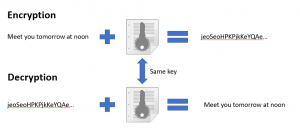
Illustration from the past
Let’s say, Bob is a British citizen spying for the Soviet Union during the Cold War. Every now and then he needs to send ciphered messages to his Russian case officer Алиса (Alice, in English). How will he do that?
First, Bob gets rid of his babysitters, catches a cab, finds himself a quiet hotel somewhere in the outskirts and composes an important message he is about to send. The next step for him is to map the message with the specific key from a plaintext to a ciphertext, which he does; then, he puts the piece of paper into a physical coin and sends the coin to Russia with some ballet dancer on tour.

Donald Duart Maclean (25 May 1913 – 6 March 1983) was a British diplomat and member of the Cambridge Five who acted as a spy for the Soviet Union.
To decrypt Bob’s message, Alice would, probably, have to meet the dancer at the Sheremetyevo airport, transport her to KGB, break the coin open and decrypt the message with the key identical to Bob’s. Phew! The operation involves a lot of people and resources.
For Bob and Alice to communicate securely in this scenario, they first have to physically meet and establish the identical key, or, maybe, transfer the key. It’s not perfectly safe. Plus, if a smart MI-6 cryptographer detects suspicious activity and intercepts the ballerina, he might decipher the message. Extremely unfortunate!
In the absence of other ways to communicate securely, though, up until the 1970s, cryptography had been based on the symmetric keys scheme. Indeed, Bob and Alice were humans back then, and, you see, to be humans was not safe!
Illustration from the present
Complicated
Blowfish is a well-known solution in modern symmetric cryptography. The Blowfish algorithm is good for a product with specific characteristics. Say, Bob doesn’t need to change the key often or are about to cipher and decipher information at high speed.
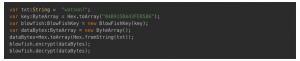
argh… what was that?
Easier
Let’s say, your product’s ecosystem is based upon interaction between Bob and your server. You receive information from Bob to keep it safe, and then give it back once he needs it. You don’t want anyone to have access to Bob’s sensitive data, so you encrypt it with the key Bob suggests (his password). Now, both of you have got the key.
Easy
1Password app for your iPhone uses Blowfish algorithm to make the Internet surfing effortless. Put it this way. Bob is tired of logging in the websites time and again. 1Password, though, keeps all his sensitive data (the passwords) on the cloud server and gives it back to Bob once he provides the app with his password (a secret key). So, now he only needs to log in once with the app, to have access to all the websites he’s logged in.
“Asymmetric encryption” – eh? Isn’t it something only Sherlock could be into?
Exactly, Sherlock could be into it! But because Conan Doyle was so dead in the 70s when asymmetric encryption became a subject for discussions, there was no-one out there to address interesting developments in a fun and engaging way.
Asymmetric cryptography is any cryptographic system that uses pairs of keys: public keys which may be disseminated widely, and private keys which are known only to the owner.
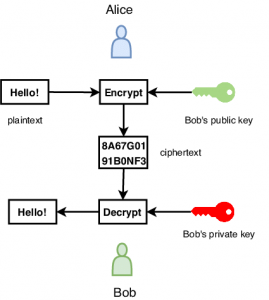
Here comes a fun part
Ladies and gentlemen, meet James H. Ellis, a British engineer who was the first one to come up with the idea of public-key cryptography.

But before we start, riddle us this. How can people exchange valuables if only one of them has got the key to the box?
![]()

The public key is born
James H. Ellis came up with an elegant solution. You should make a cut-out in the box. So that, basically, the other person really doesn’t need to have a key to put something into it. And when the secret is inside, you simply unlock the box and take the valuable out.
With this scheme, you don’t need to transport the key, you don’t need to share the key – you don’t need to do anything. Just let them know the public address of your box. Does that ring the bell? Good 🙂
When James H. Ellis only came up with this idea, he didn’t know how to implement it. Yet, his guess marked the beginning of what later turned into public key cryptography or asymmetric cryptography. And guess what? This concept is built upon interaction between Bob and Alice where they are not humans anymore.
Asymmetric encryption basics to understand
Public keys and private keys come in pairs. Their pair is called a key pair. The public key can be derived from the private key. Yes, they are a family in a way and associated with each other.
When Alice sends a message to Bob, she wants to encrypt it, right? She takes her own message, she takes the public key of Bob’s, and then she changes the initial text with multiple math functions. Finally, she sends this encrypted and irreversible version of her message to Bob. Phew! That was true math magic!
Now, remember, how 2 keys in the key pair are sort of a family? That’s the reason why Bob and only Bob can decipher this message encrypted with his public key. How can he do it? Any guesses? Right, with his private key. Now, even Alice cannot decrypt her own message! It’s only up to Bob.
Can you see why this kind of encryption is called asymmetric? Bob and Alice need each other’s keys to interact safely.
Congrats! Now you’re familiar with the small part of the technologies underlying crypto. But keep in mind that it’s just a small part of any public blockchain. Take a look at Satoshi’s description of the Bitcoin network, and you will see how transactions is just a beginning of everything!

Security question
Now, this piece was about only one thing – for you not to send a wrong key to a person who is supposed to pay you. And that’s why we need to ask you this security question.
If you want somebody to send you money, which key would you give them, a public one or a private one?
The right answer is the public key.
Hopefully, after reading this blog, you know why.
You give them the address of your magic box with the cut-out, not the key to the box, right?
Final thoughts
At this stage of reading, you, probably, can tell that there are many options for hackers to intercept the secret key if you use symmetric encryption algorithms. As we’ve had already written in the blog on Blockchain wallet, fraudsters might trick you in many different ways. For instance, they can record any information you type in with the software called keylogger. And, then, the keylogger will save information in a log file and send it to the specified receiver. Bam, your secret key is intercepted!
So, symmetric encryption comes with a huge pain point – the secret key vulnerability. This is why cryptographers from all over the world had been working hard on a mechanism where private keys didn’t need to be transferred. And they had been working good because their efforts resulted in asymmetric encryption.
Yet, unfortunately, asymmetric cryptography is not a remedy for a person who doesn’t give two hoots about online security and the safety of their private keys!
What happens to the private keys if you store them on a laptop that touches the Internet on a daily basis?
If you’re lucky enough, of course, nothing happens. But if a hacker comes across your device and detects your private keys, this will turn into a great temptation to her.
Similarly, you could write down your secret on a piece of paper and hand it out to the first person you meet in the street. Keep your private keys in the unsafe environment, and all the achievements of modern asymmetric cryptography will go to waste.
But how can you keep your private keys safe? Have a look at our previous article about crypto hardware wallets and stay tuned!
***
If you enjoyed this story, please click the  button and share to help others find it! Feel free to leave a comment below.
button and share to help others find it! Feel free to leave a comment below.
Bitcoin turns 10 years young ← P R E V I O U S
N E X T → I don’t care about KYC. Will I be OK?